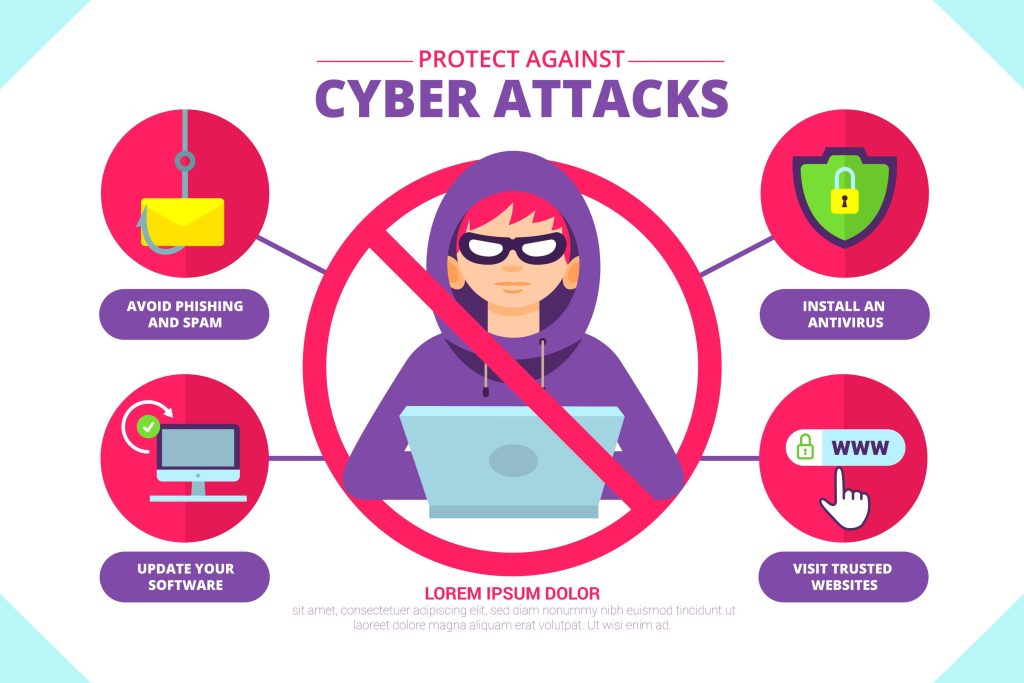
In an epoch dominated by technological prowess, the paramountcy of cybersecurity cannot be overstated. As our lives become increasingly interwoven, the perils of cyber threats loom larger than ever. This discourse navigates through the clandestine (5 Reasons Cybersecurity) hazards of disregarding cybersecurity and proffers compelling rationales for why it should ascend to the zenith of everyone’s priority register.
The Ascending Peril Landscape
The digital terrain incessantly metamorphoses, and concomitantly, so do cyber threats. From conventional phishing onslaughts to intricate ransomware tactics, the spectrum of threats perpetually widens. Recent statistical data accentuates the gravity of the situation, with a surge in cyber onslaughts across multifarious industries.
Monetary Ramifications
The repercussions of a cyber onslaught surpass immediate pecuniary detriments. Businesses and individuals confront enduring consequences, comprising impaired credit scores, legal expenditures, and escalating insurance premiums. Cognizance of the fiscal ramifications underscores the exigency for robust cybersecurity protocols.
Tarnished Reputation
5 Reasons Cybersecurity
Data breaches of eminence recurrently seize headlines, inflicting irreparable harm on an organization’s reputation. This exposition delves into real-world exemplars, elucidating how reputational impairment can transcend the inaugural incident and impact customer reliance and fidelity.
Juridical Consequences
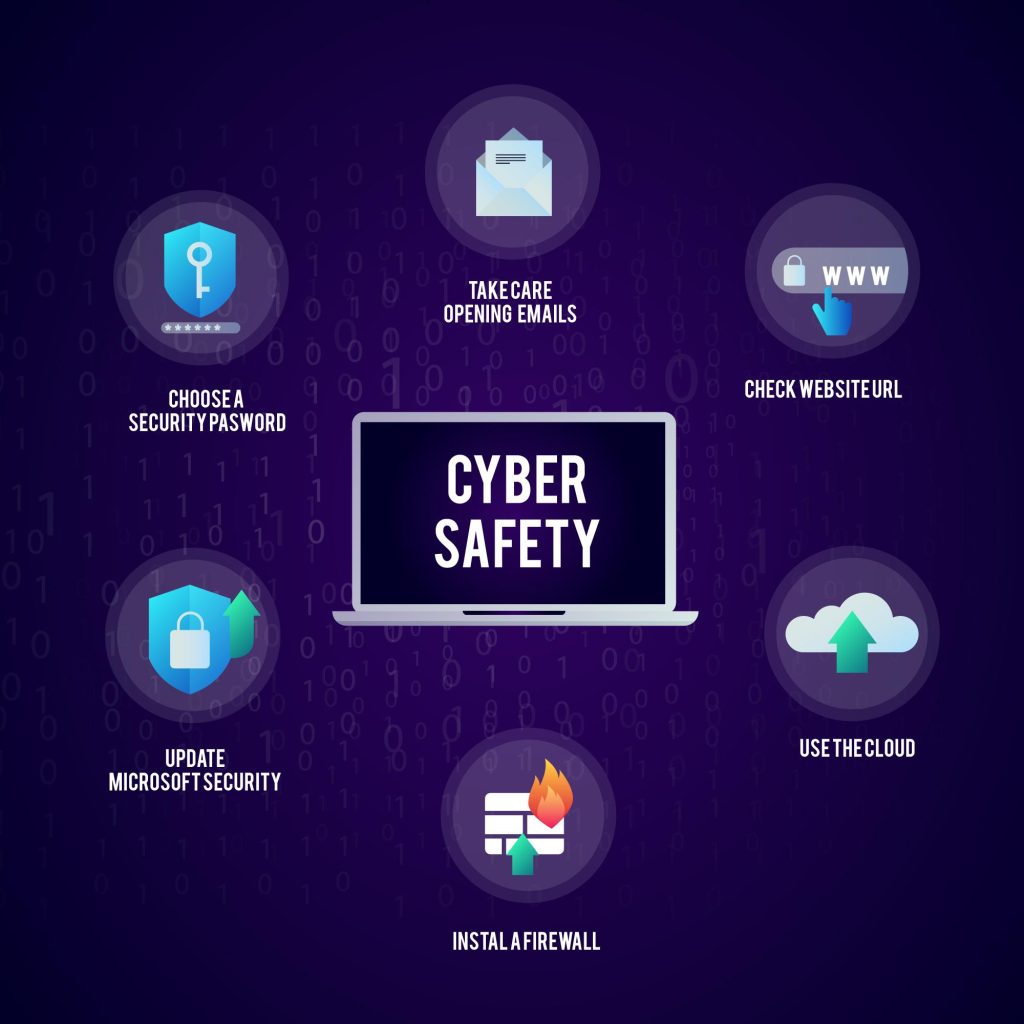
5 Reasons Cybersecurity Should
As governments worldwide fortify regulations, non-adherence to cybersecurity standards can precipitate severe legal repercussions. Organizations must be cognizant of the legal panorama and adopt preemptive measures to forestall legal ramifications.
Safeguarding Personal Data
The value of personal information in the digital epoch cannot be overstated. This discourse propounds pragmatic steps individuals can undertake to shield their personal data, accentuating the significance of preemptive measures.
Significance for Modest Enterprises
Contrary to prevailing misconceptions, modest enterprises are not impervious to cyber threats. The discourse explores economical cybersecurity measures tailored to the exigencies of smaller entities, underscoring the significance of prioritizing security.
5 Reasons Cybersecurity Should

Personnel Training
Human fallibility remains a substantial contributor to cybersecurity breaches. The discourse expatiates on the imperative nature of comprehensive training regimens for personnel, endowing them with the acumen to discern and counteract potential threats.
Sophisticated Persistent Threats (APTs)
Sophisticated Persistent Threats epitomize a refined manifestation of cyber assault. Comprehending the methodologies employed by malefactors is pivotal for organizations seeking to fortify their defenses against these persistent and pinpointed threats.
The Function of Synthetic Intelligence

5 Reasons Cybersecurity Should
Synthetic Intelligence assumes a pivotal role in contemporary cybersecurity. The discourse explores how AI augments threat identification and riposte, proffering a proactive modus operandi to cybersecurity in an epoch of ceaselessly evolving threats.
The Imperative for Regular Updates
Routine software updates constitute a foundational facet of upholding a secure digital milieu. The discourse underscores the significance of expeditious updates and efficient patch management to alleviate vulnerabilities and amplify overall security.
Collaboration and Information Exchange

5 Reasons Cybersecurity Should
In the ever-fluid panorama of cyber threats, industry-wide collaboration is paramount. The discourse spotlights the role of information exchange and collaboration in crafting a unified front against cyber malefactors.
Balancing Security and Convenience
Attaining equipoise between robust security measures and user-friendly experiences is a conundrum. The discourse explores user-friendly security measures and the significance of striking the right equilibrium for widespread user adoption.
The Tomorrow of Cybersecurity
Peering into the future, the discourse delves into nascent threats and innovations in cybersecurity technology. Staying abreast of the evolving landscape is imperative for organizations and individuals alike.
5 Reasons Cybersecurity Should

Conclusion
In summation, prioritizing cybersecurity is not merely discretionary; it is a prerequisite in our digitally impelled world. The discourse encapsulates key takeaways and implores readers to accord cybersecurity top-tier status to safeguard their personal and professional spheres.
- Top 10 Compelling Reasons Cybersecurity
- Bulk Email Checker Tools
- Unveiling the Secrets: Mastering Email Checkers for Ultimate Inbox Control!
- Garmin Network Cable: Navigating the Path to Seamless Connectivity
- Long Range WiFi Extender Outdoor: Improving Availability Past Walls
FAQs for Reasons Cybersecurity
How can diminutive enterprises defray cybersecurity measures?
Diminutive enterprises can probe into cost-effective cybersecurity solutions tailored to their requisites. Many security implements tender scalable alternatives, permitting businesses to remunerate for the echelon of protection they necessitate.
What function does personnel training fulfill in cybersecurity?
Comprehensive personnel training is pivotal for mitigating the hazard of human fallibility, a ubiquitous factor in cyber onslaughts. Training regimens edify personnel about potential threats and endow them to recognize and respond judiciously.
Why is AI pivotal in cybersecurity?
Synthetic Intelligence amplifies threat detection and riposte by scrutinizing copious data expeditiously. Its capacity to pinpoint patterns and anomalies contributes to proactive cybersecurity measures.
How frequently should software updates be executed?
Regular software updates are pivotal and should be executed promptly. Companies and individuals should espouse a proactive approach to patch management to mitigate vulnerabilities and enhance overall security.
What can individuals undertake to shield their personal data?
Individuals can undertake preemptive measures such as employing robust, unique passwords, enabling two-factor authentication, and exercising caution about divulging personal information online.